A Chinese state-sponsored hacking group is hitting air-gapped systems of industries in Eastern Europe, says Kaspersky researchers in a new report.
The threat actor, tagged as APT 31, is found using multiple implants throughout it’s hacking process. Some of which can load malware directly into system memory and steal data discreetly and export the files to hackers’ C2 sophisticatedly.
Chinese APT Stealing Sensitive Data
This week, researchers at Kaspersky detailed a new campaign led by Zirconium(a Chinese hacking group known as APT 31), targeting air-gapped industrial systems in Eastern Europe.
Researchers first discovered the campaign in April last year, which involved three separate stages. The first includes establishing and maintaining persistent remote access to the compromised systems and collecting valuable data for surveillance.
In the second stage, APT 31 drops specialised malware to steal data from air-gapped systems using USB propagation. Air-gapped systems are disconnected from the public internet and even from specific networks that may be vulnerable to hacks.
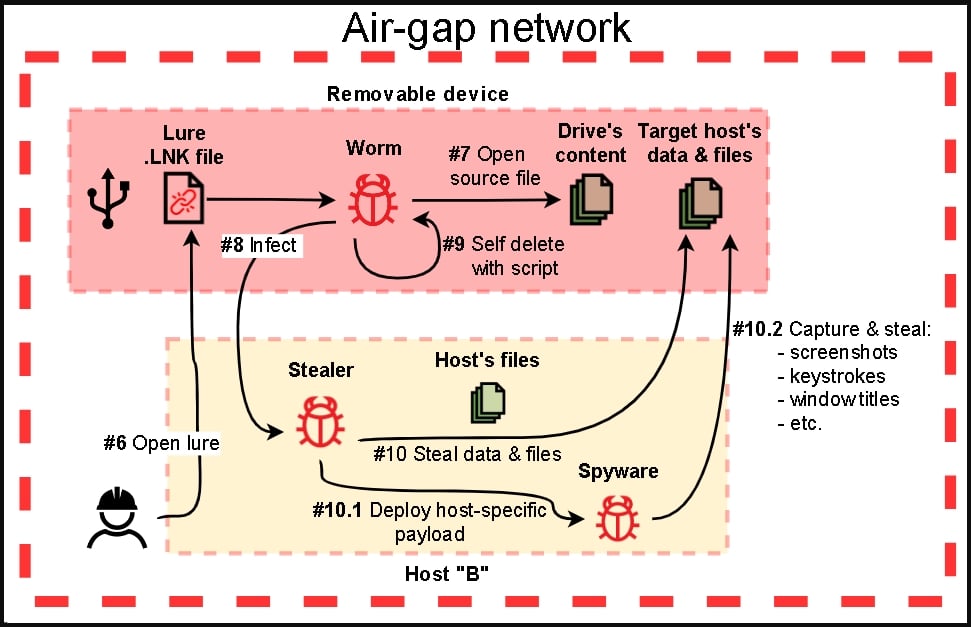
And in the third stage, hackers use implants to upload the collected data to their C2 servers. Researchers noted 15 different implants throughout the hacking process, each having other purposes. A notable one among them is a specialised malware that can decrypt and inject the payload into a legitimate process’s memory – to evade detection – and proceeds to steal sensitive files after a 10-minute sleep.
To avoid interception, the stolen files are archived using WinRAR and shared to Dropbox to make the traffic seem legit. Researchers shared the malware hashes, a complete set of indicators of compromise and other technical details to detect and avoid this attack.
Other Trending News:- News








